AuthBreaker - A tool for automated & targetted authorisation testing in Burp Suite
AuthBreaker is a Jython based Burp Suite extension we put together to streamline authorisation testing in web apps and APIs, particularly when evaluating how applications handle role-based access control. Instead of leaving the tester to manually repeat requests and swapping session cookies or tokens, AuthBreaker automatically modifies and re-sends requests using a different user context.
Additionally, AuthBreaker also provides ‘Sniper’ functionality that allows a user to target specific requests, or batches of important requests, which can then be automatically sent to Repeater for specific attention.
Installation & Configuration
Download the Jython file from our GitHub repository and load it into Burp. A new tab should appear in your console.
In the “Settings” tab of the plugin, insert the domain you’d like to investigate. It is specific, so “example.com” will only inspect/modify traffic for that domain and not *.example.com. Once you’ve set the target you can modify the Replacement Rules section. An example, such as the following will replace an “Authorization” header with a new bearer token. Once you understand this format, you can apply it to any header you desire.
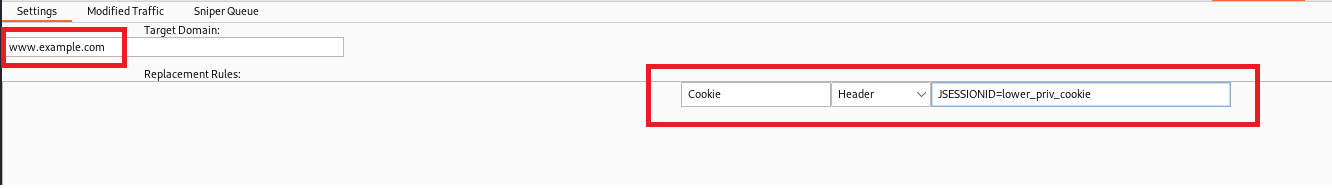
Using the Plugin
Consider a random web application with three roles: Admin, Manager, and User. You log in as Admin and begin navigating the site, editing profiles, accessing dashboards, deleting records etc. AuthBreaker automatically replays those admin-level requests using session cookies from a basic User account configured in the extension settings. Each request is silently replayed and the results from this traffic can be identified in the “Modified Traffic” tab of the plugin:
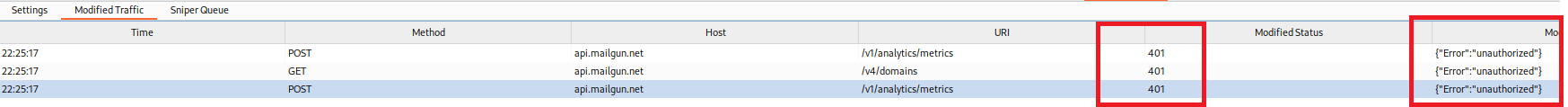
If the responses from the application are the same or very similar, this may indicate an authorisation issue that requires further investigation. Obviously every application is different and the analysis of the output is left to the user to review for potentially security issues.
Sniper Queue
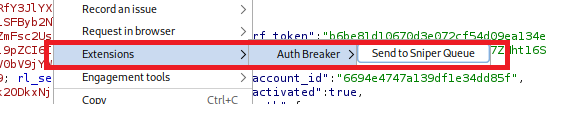
For more targeted testing, the Sniper Queue allows you to select specific requests (or sets of requests) rather than automatically modifying everything and spamming it out. To use this, right-click on a request in Burp and send it to the AuthBreaker Sniper Queue:
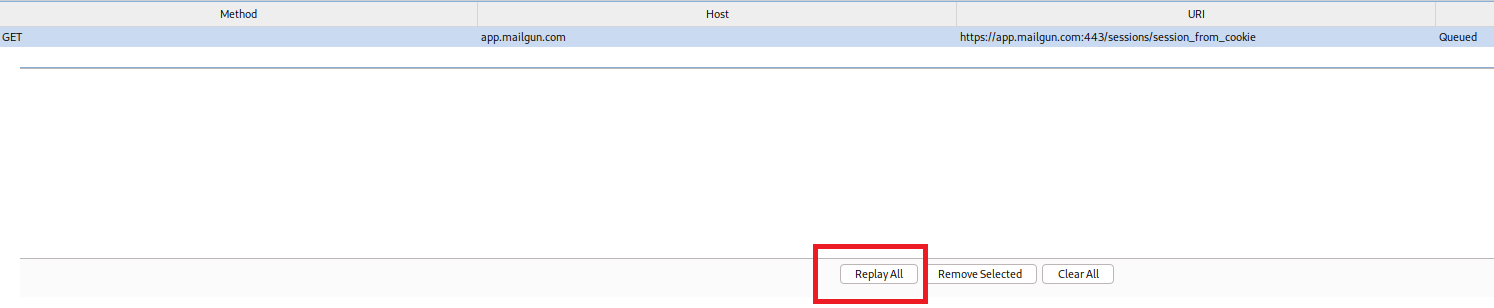
The requests can be sent to the Repeater tab with the automatically modified header, via the “Replay All” button:
Final Thoughts
There are plenty of other tools out there with similar goals, but I wanted something with my own layout and ideas. If you're working on authorisation testing and want a practical, time saving plugin to identify access control weaknesses that you ordinarily miss, give AuthBreaker a try and let me know how it works for you.